Bringing Order to Chaos
Protecting IT/OT environments can often feel like chaos. Let us assess and protect your business by turning chaos into a manageable risk environment.
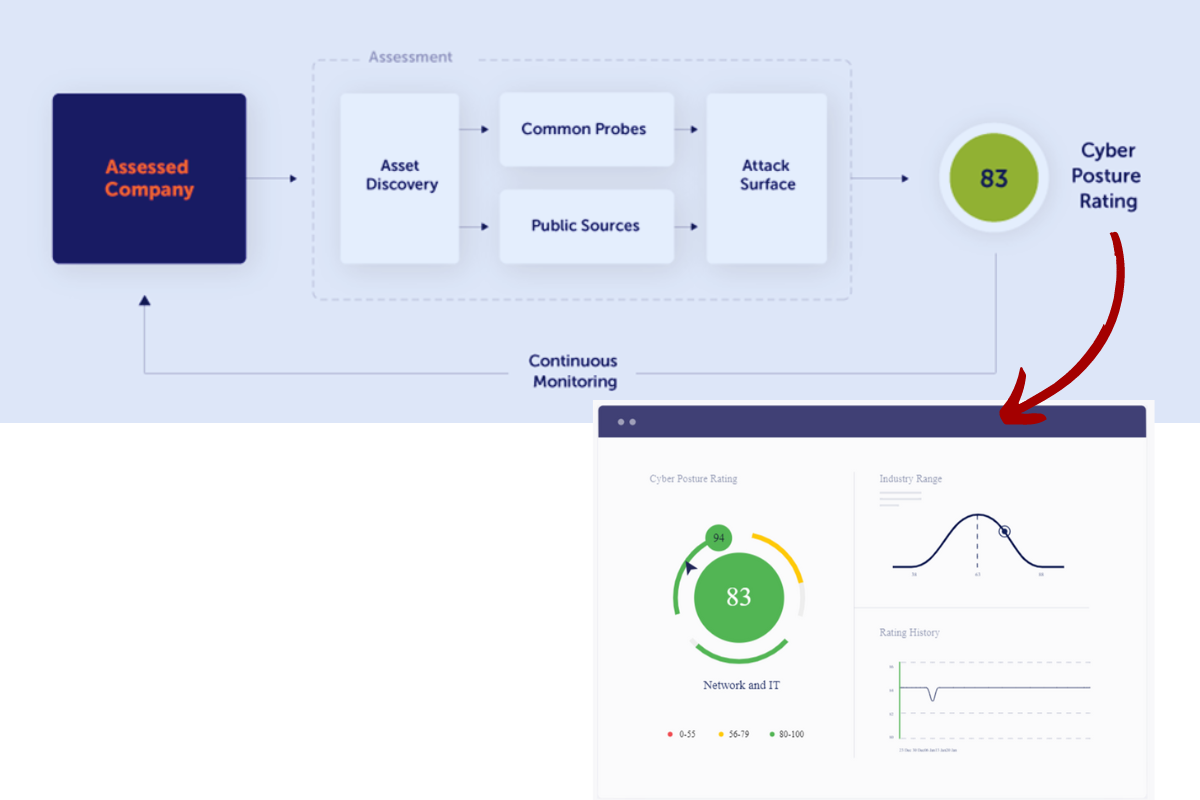
CyberSafe Assessment
Get a fast and accurate overview of the security of your organization. We pull data from over 1,000 sources and analyze it to reveal your true level of cyber resilience. Gain ongoing visibility, insight and control!
Path to CyberSafe
After the CyberSafe Assessment, there are options depending on your risk level and goals. We offer advisory and remediation services and can work with insurance providers to help you obtain cyber insurance.
CyberSecurity Solutions
We specialize in customizing IT and OT solutions to protect, support and secure companies both large and small. From security monitoring to incident response to security training, we have you covered!
Companies invest heavily in cybersecurity but are still breached.
Are you among the 86% of businesses with either no or extremely limited visibility into your IT/OT environment? Does trying to understand and control the risk in your digital environment seem overwhelming?
Security is something that needs to be built into complex IT/OT systems
Through our expertise as asset owners and operators, we understand how to build protection into these complex environments and prevent attackers from impacting operations.
We also have extensive federal and DoD experience. Learn More About Our Federal Solutions

Chaos is a joint venture between two companies at the forefront of cybersecurity, working hand-in-hand to provide one of the most comprehensive cutting-edge solutions in the industry. Learn More.
IT and OT Cybersecurity Experts
Our experts have decades of IT and OT experience. We operate at the highest level, designing cybersecurity programs and fighting advanced persistent threats for the DoD. Our experts know what it takes to manage risk.
The Chaos Team has the experience, skills, and understanding to deliver what it takes to identify and manage risk and bring order to Chaos for our customers. Leave the security to us, while you focus on the core of your business.
Securing Data, Systems & Networks
As proven experts, we are led by field-experienced OT/ICS integrators, seasoned IT and OT security experts, senior security researchers, operators, analysts, red teamers, and threat hunters with extensive commercial, military, and industry experience. We bring unique security solutions based on deep insights into sector-specific threat and vulnerability mitigation solutions.
Advise
Review current security posture and provide options to enhance risk management.
Assess
Take a purple team approach to identify risk to your OT/IT network and systems.
Remediate
Provide a full range of options and training to mitigate identified concerns and risk.
Monitor
Provide proactive detection and reporting of security threats through an IT/OT SOC.
Respond
Respond to monitored and reported events via remote and deployed resources to address trouble reports.
Train
Build security awareness and ensure client team members have the right knowledge and skills for daily operations.


Attacks are not all the same; Why should your protection be?
Your OT infrastructure is very different from your IT infrastructure. Broad brush approaches and threat monitoring are not enough to protect you. Only security experts who understand OT can help you achieve cost-effective security to your OT infrastructure.
Specialized solutions designed for your architecture
Flexible solutions that help you identify and control risk within your security budget
Our experienced Cyber team can take some of the most complex problems and simplify it to create a comprehensive security solution
See Where You Stand with Our CyberSafe Assessment
CyberSafe is an automated, fact-based assessment and mitigation recommendation tool that delivers a objective, mitigated risk rating. CyberSafe is a time- and energy-saving continuous risk management system that offers clients on demand access to their company’s cyber risk profile It aligns with ongoing state, federal, legislative, and DoD efforts, and our work will continue to shape and drive state and federal efforts to optimize the cyber insurance process.